SSL Certificates for Instances
Users might need to obtain certificates for their instances to secure i.e. web servers. We recommend using Let's Encrypt certificates for your instances. This can be done in multiple ways, but we we will show two ways here in this guide.
Option 1: Automated using Ansible
The team at h-da.cloud provides an Ansible role that can be used to obtain certificates and setup auto renewal
for the obtained certificates. This role can be found in GitLab. To use this role with
Ansible add it to a requirements.yaml file in the following way:
These requirements can then be installed using the command ansible-galaxy install -r <path_to_requirements>.
Creating a playbook
When the role is installed create a simple playbook that runs the role. This can be done in two ways. Either via le-go or certbot depending on whether you make use of the DNS challenge or a standalone web server to obtain the certificates.
We recommend this approach due to the fact, that you do not need to open up any ports on your instance
in order to obtain certificates. Furthermore, using a DNS challenge instead of the web server makes it
possible to obtain certificates for h_da internal services (i.e. instances with *-hdaonly security groups).
This guide shows how to make use of the OpenStack DNS servers within your project's zone to complete the ACME DNS challenge. In order to use this mode, you need to create an application credential first.
Creating an Application Credential
An application credential can either be obtained via the CLI or the web dashboard
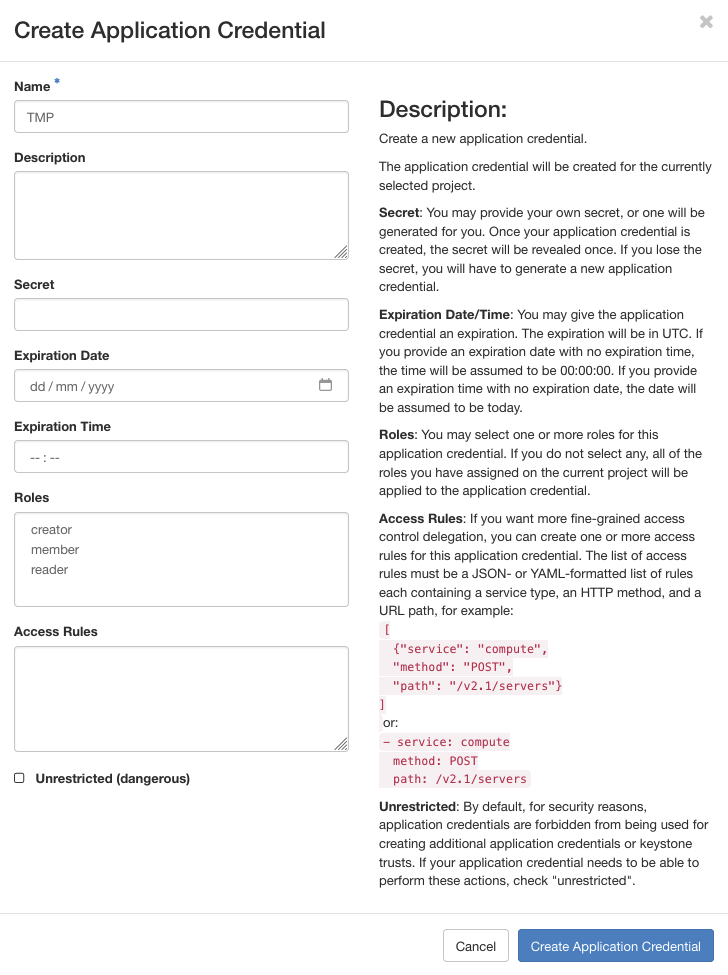
Head over to Identity Application Credentials. Here click the
+Create Application Credential button on the right. In the dialog enter a name and confirm.
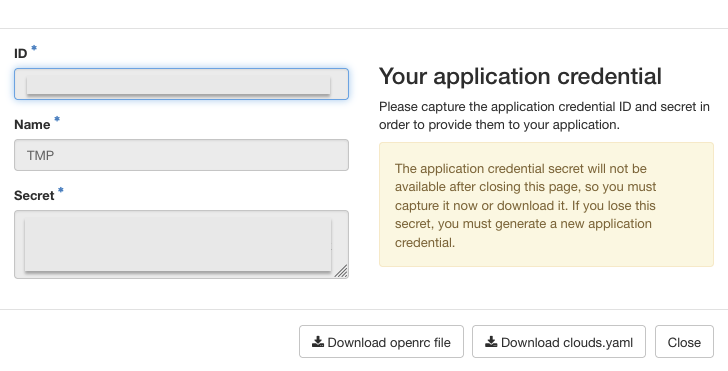
When the credential is created it will show you the secret's ID as well as the secret itself.
Important
Take note of the application credential's secret here and store it somewhere safe, as you will not be able to access it again. For Ansible consider storing it in an Ansible Vault.
If you have not set up CLI access before, follow this guide and then return here. An application credential can then be created with the following command:
Important
Take note of the application credential's secret here and store it somewhere safe, as you will not be able to access it again. For Ansible consider storing it in an Ansible Vault.
Using the Ansible Role
Take the following task as an example:
- name: Obtain LE Certificates
ansible.builtin.import_role:
name: hdacloud.certs
vars:
cert_fqdns:
- "{{ your_fqdn }}"
admin_email: "<email>"
dns_challenge: true
lego_version: "4.11.0"
lego_dns_provider: "designate"
dns_provider_auth_env_variables:
OS_AUTH_URL: "https://h-da.cloud:13000"
OS_REGION_NAME: "eu-central"
OS_AUTH_TYP: "v3applicationcredential"
OS_APPLICATION_CREDENTIAL_ID: "{{ os_application_credential_id }}"
OS_APPLICATION_CREDENTIAL_SECRET: "{{ os_application_credential_secret }}"
This task will create a certificate for your provided FQDN using your previously created application credential. If you need the certificate to be valid for multiple FQDNs just add them to the list. However, if you need a single certificate per FQDN you will need to run the role in a loop.
More information on the role parameters can be found in it's repository.
When your certificates were obtained correctly you can find them here: /var/lib/lego/certificates/${your_fqdn}.*.
If you do not want to use the DNS challenge the role also implements a different way to obtain certificates using either a standalone web server provided by certbot or an existing one to complete the process of obtaining the certificate.
This requires your instance to allow inbound traffic on port 80. For this you might need to add a
security group to your instance.
Using the Ansible Role
Depending on if you are running a web server on your instance already the variables passed to the ansible role differ slightly.
This task will create a certificate for your provided FQDN using your previously created application credential. If you need the certificate to be valid for multiple FQDNs just add them to the list. However, if you need a single certificate per FQDN you will need to run the role in a loop.
More information on the role parameters can be found in it's repository.
When your certificates were obtained correctly you can find them here: /etc/letsencrypt/live/${your_fqdn}/.
Option 2: Using certbot by itself
If you are not comfortable in using Ansible or just do not want to use the role, you can also use certbot by itself on your instance. As certbot provides a quick guide on how to use it to obtain a certificate and make it work with most of the common web servers, we will not go into detail here.
The certbot guide is available at certbot.eff.org/instructions. Here you can select your web server as well as the operating system you are running and will be provided with a quick guide to obtain a certificate.
Closing words
Obviously you can choose to obtain certificates in a different way than the options described here. This guide only serves as an orientation. However, note that the certificate functionality of the SD-Tool should not be used for OpenStack instances.